One of the more potentially disruptive and destructive viruses you’re likely to run into—and that goes for everyday users and IT experts alike---is circulating around the country at a troubling rate. It can be quite costly to deal with both in terms of time and money and has the ability to cripple a given department or even an entire business. We have seen this virus at one of our unmanaged clients. Unmanaged meaning they don't have our recommended firewall, or spam filter in place. A user received one of the trick emails and opened it . . We were providing this client with managed backups so we were able to restore the data from their Server and we had to reinstall the workstation from scratch. One click cost this firm over $1000.00 in professional services fees!
Named ‘CryptoLocker’, the virus is typically spread by means of email attachment and disguised as an MS Office, PDF, or JPEG file—though it has been distributed in other less common file formats as well. It may get delivered and appear as though it has come from someone the receiver knows or a trusted business entity such as UPS, FEDEX, or a major banking institution. The best defense given these circumstances is to avoid opening any attachments you are not expecting and certainly none from anyone you do not trust. Texting a contact and asking if they sent you an attachment might be thought of as the proverbial ‘ounce of prevention’---and well worth it.
THE DAMAGE IT CAUSES
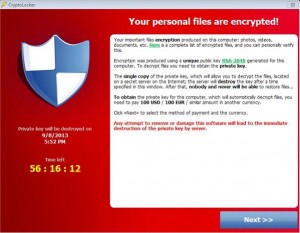
When the attachment is opened the CryptoLocker virus immediately encrypts files—including those with financial or other information such as spreadsheet and text editing programs (think MS Excel, Word, and PDF pretty much everything you would want to open ). It then posts a banner on the computer screen indicating that you have 72 hours to pay between 300 and 700 dollars to get the files decrypted. If that time passes and a payment isn’t made or if you simply remove the virus then the encrypted files are basically gone for good. The encryption the virus uses was developed for government use, is quite effective, and isn’t known to be breakable (the NSA might be able to do it but they aren’t sharing). Particularly troubling in some cases is that if the computer that gets infected has shortcuts to or mapped network locations/folders/drives—such as those on network servers---the files at those locations can get encrypted too. This means the potential exists for say entire legal or accounting departments to come to a grinding halt---and while paying the ransom is known to actually work where decrypting the files on the infected computer is concerned, decryption of affected network locations is less of a certainty.
Here is a screenshot of the ransom message:
What Can you do to protect your self you might Ask?
- Don't use your computer (Just Kidding although that would work)
- Be vigilant when using email and the internet in general the bad guys are tricky and they send messages that look like they are from someone you know, but if you look a little deeper you can often see they are scams.
- If you aren't expecting an attachment. STOP! Ask if you were expecting this?, Do you need it for work? Does something seem odd?, Call the person or email them back asking if they sent the attachment.
- Contact Albright Networks and ask our Team to have a look we can remote into your system and quickly look, (even if your not a managed client), Call our Help Desk # 360.797.5232
- Consider an upgraded firewall, and hosted email with cloud based spam filtering these are all options we offer to our clients. We can give you a free consultation any time.
Update: I actually did an automatic post on this on the 24th. it contains more detail and is just a few posts down please scroll down if you want more information..